What is Cloud Computing?
First, a brief explanation, so we’re all on the same page, of what Cloud Computing actually is.
NIST has defined Cloud service characteristics but, given this definition is nearly seven years old as of this writing, one would not be blamed for thinking the definitions are well understood. However, we have found this is not the case.
NIST describes Cloud services as having the following essential characteristics:
- On-demand self-service
A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service provider. - Broad network access
Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogenous thin or thick client platforms (e.g., mobile phones, tablets, laptops, and workstations). - Resource pooling
The provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to consumer demand. There is a sense of location independence in that the customer generally has no control or knowledge over the exact location of the provided resources but may be able to specify location at a higher level of abstraction (e.g., country, state, or datacenter). Examples of resources include storage, processing, memory, and network bandwidth. - Rapid elasticity
Capabilities can be elastically provisioned and released, in some cases automatically, to scale rapidly outward and inward commensurate with demand. To the consumer, the capabilities available for provisioning often appear to be unlimited and can be appropriated in any quantity at any time. - Measured service
Cloud systems automatically control and optimize resource use by leveraging a metering capability at some level of abstraction appropriate to the type of service (e.g., storage, processing, bandwidth, and active user accounts). Resource usage can be monitored, controlled, and reported, providing transparency for both the provider and consumer of the utilized service.
(Source: NIST SP 800-145, The NIST Definition of Cloud Computing)
The eXtensile Hybrid Cloud Difference
eXtensile Hybrid Cloud
Hands-off Hosting
eXtensile Hybrid Cloud resources are managed on Logical Front’s data center by our experts. The result: the most cost-effective cloud solution.
- Managed hosting, allowing your staff to focus on the important things
- Erase downtime with tier 4 data center functionality
eXtensile Hybrid Cloud Burst
Meet User Demand
eXtensile Hybrid Cloud Burst resources are hosted in the most cost-effective way possible while also maintaining on-premise capability.
With eXtensile Burst,when cyclical loads are needed, they can burst into a tenanted Public Cloud environment.
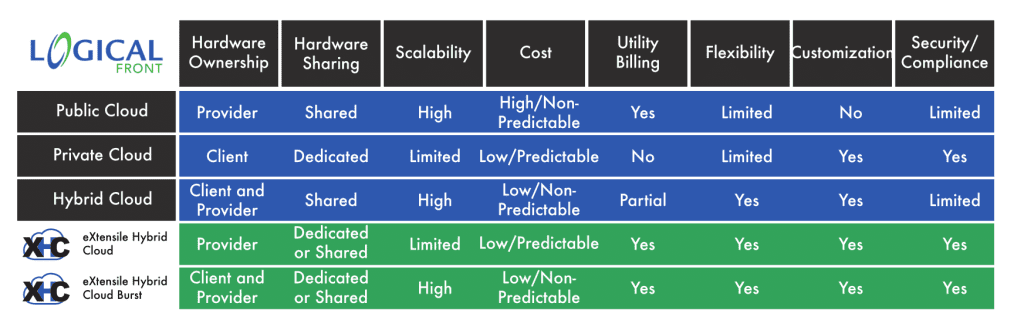
In order to properly have a discussion about eXtensile Hybrid Cloud, it is important to understand traditional Cloud Computing models: Public, Private, Community, and Hybrid. Cloud computing can be a tricky affair, as each scenario varies. Each form of cloud also differs in their strengths and drawbacks, compared in the following chart:

eXtensile Hybrid Cloud (XHC)
eXtensile Hybrid Cloud can be used to host all resources, yielding the least cost, greatest supportability, and least complexity. Your network is accessed through secure channels defined by you. Another option is to host some resources on-site and the remainder/specific loads on XHC. Accessibility is defined either holistically or application-by-application.

EXTENSILE HYBRID CLOUD BURST (XHCB)
One of the reasons the eXtensile Hybrid Cloud Burst (XHCB) solution is much less expensive is its burstable nature. XHCB resources are hosted in the most cost-effective way possible, and then when cyclical loads are needed, they can burst into a tenanted Public Cloud environment.
In a recent study for a Texas-based college, it was found that using eXtensile Hybrid Cloud with bursting capabilities would cost less than half of doing it themselves. It should be noted that going all public cloud would also have been more than double a traditional implementation as illustrated above.
DaaS (Desktop as a Service) Powered by XHC
Logical Front offers desktop as a service (DaaS) running on eXtensile Hybrid Cloud. This utilizes Virtual Desktop Infrastructure (VDI) technologies on proven platforms and practices while providing the most stability, security, and supportability. XHC DaaS reduces and often eliminates on-site support and maintenance costs.
A Note About Security
One of the guests on stage at Citrix Synergy last year with Citrix’s CEO, Kirill, was Jim Noga, Chief Information Officer of Partners Healthcare in the Northeast. Jim said something that struck a significant chord. He said to the effect that Azure and Citrix as providers are much better at Cyber-security than any individual organization. Now, instead of being a security risk, the right cloud solutions are now ways for us all to secure our environments, their functions, and importantly, their data. These organizations can participate with us through our audits and/or provide their own internal or regulatory audit documentation.
The Decision Process

Logical Front recommends utilizing Gartner’s five-phase investigation process when deciding to move resources to cloud computing models. Logical Front can help with all of these stages and has an Assessment process to assist. Depending on the size of the organization and the proposed project, these steps can be tailored larger or smaller in order to fit what makes sense for the effort. However, all steps should be included.
- Build the business case
Link the Key Initiative to the overall drivers or objectives of the business. Gain support from senior business leaders and senior stakeholders. Set a baseline for assessing the impact of the investigation. Estimate costs and resource requirements. - Develop the strategy
Align the investigation with the business strategy, and show how it can deliver business value. Show how the investigation might lead to changes that will affect your business environment. Work with key stakeholders to identify business needs. - Assess readiness
Identify the budgetary, staffing, technology and other requirements necessary to prepare the business for the investigation. Develop a total cost of ownership analysis framework. Review established policies for assessing risk and managing governance. - Pilot or prototype
Identify a group to pilot, or develop a prototype for the investigation. Develop and communicate detailed requirements. Manage the pilot/prototype. Assess and communicate the results. - Gain approval
Analyze findings of the readiness assessment and pilot or prototype effort, and revise the strategy and business case accordingly. Present findings of the investigation to senior stakeholders and business leaders.
(Source: Cloud Computing: Key Initiative Overview by David W. Cearley, Research Vice President and Gartner Fellow, Gartner)